Fifty Enterprises Breached Without a Single Exploit
Why it matters: A lone cybercriminal has compromised approximately 50 major organisations — including defence contractors, airlines, and military healthcare providers — using nothing but stolen passwords purchased from dark web markets. Every single victim failed to enforce multi-factor authentication. This campaign proves that the most devastating breaches require no technical sophistication when basic security controls remain absent.
The campaign that required no hacking
Between 2021 and January 2026, a threat actor operating under the aliases “Zestix” and “Sentap” systematically breached cloud file-sharing platforms at dozens of global enterprises. The attack methodology was remarkably simple: purchase stolen credentials from infostealer malware logs, attempt login, succeed because no second authentication factor existed [1].
Hudson Rock’s investigation, published 4 January 2026, confirms that none of the compromises exploited software vulnerabilities. No zero-day exploits. No sophisticated attack chains. No advanced persistent threat techniques. The entire campaign relied on a single organisational failure: the absence of multi-factor authentication on cloud storage platforms [1].
The platforms targeted — ShareFile, Nextcloud, and OwnCloud — all support robust security features including MFA enforcement. The technology existed. The victims simply chose not to use it.
The uncomfortable truth: stolen passwords combined with absent MFA equals guaranteed access. Every time.
What was exposed
The confirmed victim list reads like a catalogue of sensitive sectors. Pickett & Associates, a US engineering and defence contractor, lost 139.1 gigabytes of data including classified LiDAR files, transmission line maps serving American utilities, and defence blueprints [2]. Transmission network maps in adversary hands enable infrastructure targeting. Classified content suggests active defence department contracts were compromised.
Intecro Robotics, a Turkish aerospace manufacturer, suffered exposure of 11.5 gigabytes of military intellectual property. This included UAV and fighter jet blueprints — strategic state secrets now circulating through criminal markets [2].
Iberia Airlines, part of International Consolidated Airlines Group, lost 77 gigabytes of aircraft maintenance programs, fleet management data, and technical specifications. Attackers with detailed knowledge of maintenance procedures can identify sabotage opportunities and aircraft vulnerability patterns [2].
Perhaps most troubling: Maida Health, a Brazilian military healthcare provider, exposed 2.3 terabytes of patient medical records, personally identifiable information, and military personnel healthcare data. Medical records enable identity fraud, blackmail, and targeted espionage against government officials [2].
Additional confirmed victims span mass transit manufacturing, telecommunications, legal services, government infrastructure agencies, and logistics companies. The common thread is not sector or geography but a shared security posture failure.
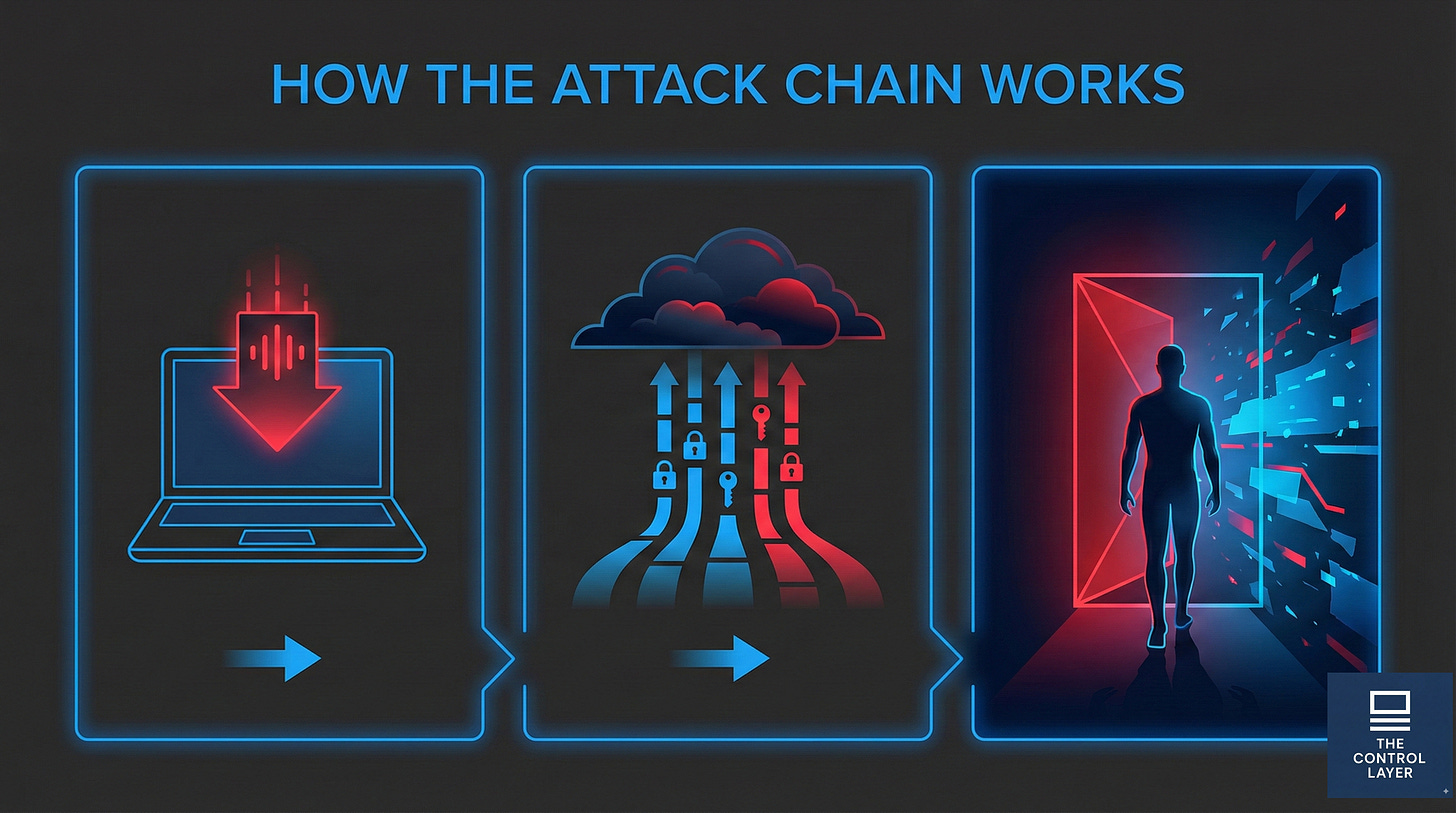
How the attack chain works
The campaign follows a three-stage sequence that security professionals will find depressingly familiar.
Stage one: infection. Employees inadvertently download malicious files containing infostealer malware — typically RedLine, Lumma, or Vidar variants. Delivery mechanisms include phishing campaigns and trojanised software downloads. The malware executes silently on the victim’s device [1].
Stage two: credential harvesting. The infostealer extracts saved usernames and passwords from browser storage, session cookies, autofill data, and VPN credentials. This data exfiltrates to attacker command-and-control servers within seconds. The malware then terminates, leaving minimal forensic footprint [3].
Stage three: opportunistic exploitation. Zestix purchases aggregated infostealer logs from dark web marketplaces, then searches specifically for corporate cloud file-sharing platform URLs. Using harvested credentials, the actor attempts authentication. Because targets failed to enforce MFA, login succeeds with only the stolen password. The attacker then browses, collects, and exfiltrates sensitive data at leisure [1].
The attack maps cleanly to MITRE ATT&CK techniques: T1078 (Valid Accounts) for initial access and defence evasion, T1555 (Credentials from Password Stores) for credential access, T1213 (Data from Information Repositories) for collection, and T1567.002 (Exfiltration over Web Services) for data theft [3].
The temporal asymmetry problem
A critical finding underpins the campaign’s success: credential latency. Many passwords exploited by Zestix had been present in infostealer logs for multiple years prior to exploitation [1].
This reveals a systemic failure in credential lifecycle management. Organisations neither rotated passwords nor invalidated sessions despite years of evidence that employee devices had been compromised. What should have represented a temporary security incident became a persistent vulnerability.
The asymmetry favours attackers absolutely. Threat actors can wait indefinitely for favourable conditions — a compliance gap, a security team transition, a pandemic-driven remote work expansion. Defenders must maintain perfect security continuously. When credentials sit unrotated in criminal databases for years, attackers simply choose their moment.
Who else is at risk
Hudson Rock’s threat intelligence platform identified valid credentials for major enterprises currently circulating in infostealer logs. Organisations including Deloitte, KPMG, Samsung Electronics, Honeywell International, Walmart, and the US Centers for Disease Control and Prevention have employee credentials exposed [2][3].
These organisations were not directly victimised by Zestix — yet. Their exposure in infostealer logs represents critical vulnerability absent immediate MFA enforcement.
A comprehensive study of infostealer infections found internal credentials in 78% of recently breached companies within six-month windows of compromise [4]. This indicates endemic endpoint infection at scale across enterprise environments. The question for most organisations is not whether employee credentials have been stolen, but whether those credentials provide value to attackers.
Analysis
The Zestix campaign exposes a paradox that should trouble every security leader: the most devastating attacks require no technical sophistication. No zero-days, no exploit chains, no advanced techniques — simply stolen passwords combined with organisational failure to implement basic controls.
This is simultaneously reassuring and damning. Reassuring because the remediation path is clear and immediately actionable. Damning because it demonstrates that organisations with substantial security budgets, compliance certifications, and dedicated security teams still fail to implement table-stakes authentication controls.
The 100% correlation between MFA absence and successful compromise is not coincidence. It is causation. MFA represents the single most effective control against credential-based attacks. By requiring a second authentication factor, MFA invalidates the threat model Zestix exploits entirely.
For UK mid-market organisations, this campaign offers a clarifying lesson. Enterprise-grade security does not require enterprise budgets. Basic controls — MFA enforcement, credential rotation, endpoint detection — deliver measurable protection against the actual threat landscape. The Zestix campaign succeeded not because victims lacked resources but because they failed to deploy resources already available to them.
Risks and constraints
Several factors complicate straightforward remediation.
Legacy system limitations. Some older cloud platforms and on-premises systems lack native MFA support, requiring additional identity provider integration or platform migration.
User resistance. MFA introduces friction into authentication workflows. Organisations must balance security requirements against user experience, particularly for high-frequency access patterns.
BYOD exposure. Hybrid work environments mean employees access corporate cloud systems from personal devices outside organisational security controls. Infostealer infections on personal devices compromise corporate credentials regardless of endpoint protection on managed devices.
Detection gaps. Infostealer malware typically accomplishes its objective in seconds before terminating. Behaviour-based detection struggles with threats that complete execution before patterns emerge.
Scope uncertainty. Organisations may not know whether their credentials currently circulate in dark web markets without active monitoring capabilities.
What to do next
For boards and executives: Demand MFA compliance reporting across all cloud platforms, VPN services, and remote access systems. Treat MFA absence as a material risk requiring immediate remediation, not a technical detail for IT to manage. Verify that cyber insurance policies do not exclude losses from breaches resulting from MFA failures — many do.
For technical leaders: Conduct immediate audit of MFA enforcement across ShareFile, Nextcloud, OwnCloud, and equivalent platforms. Rotate all credentials for cloud file-sharing systems and invalidate existing sessions. Deploy dark web monitoring through threat intelligence platforms to identify exposed credentials before attackers exploit them.
For mid-market organisations: Enable MFA on every cloud platform today. This single action would have prevented every compromise in the Zestix campaign. If legacy systems lack MFA support, prioritise migration or implement compensating controls. Consider credential monitoring services — the investment is modest compared to breach remediation costs.
Disclaimer: This article represents analysis based on publicly available information as of January 2026. It does not constitute legal, financial, or professional advice. Organisations should consult qualified security professionals for implementation guidance specific to their environments.
If your organisation needs support implementing authentication controls and credential management frameworks, Arkava helps companies turn security investment into measurable risk reduction.
Contact: engage@arkava.ai