When the Defenders Fall: Inside the F5 Networks Cyber Breach That Shook Global Infrastructure
How a nation-state hack on one of the world’s most trusted cybersecurity companies exposed the fragility of modern digital defences.
Why it matters
F5 Networks isn’t just another tech company. Its systems sit at the heart of the world’s digital infrastructure — protecting banks, governments, hospitals, and telecoms from attack. When F5 was hacked by a nation-state group believed to be linked to China, the breach didn’t just threaten one vendor — it threatened the digital nervous system of modern society.
What Happened
On 15 October 2025, F5 Networks confirmed that sophisticated hackers had maintained long-term, undetected access to its internal systems for more than a year.
The attackers stole portions of their BIG-IP source code, product vulnerability information not yet disclosed publicly, and some customer configuration data — effectively giving them the keys to thousands of networks worldwide.
BIG-IP is F5 Network’s flagship family of hardware appliances and software, it sits between end users and an organisation’s servers.
BIG-IP is like an intelligent traffic cop that not only directs vehicles (network packets) to their destinations but also inspects them for threats, optimises their routes, enforces security policies and ensures critical applications remain available even during cyber attacks or failures.
The US Cybersecurity and Infrastructure Security Agency (CISA) issued Emergency Directive 26-01, forcing all government agencies to patch F5 devices within a week. The UK’s National Cyber Security Centre (NCSC) followed suit, warning British organisations to check their F5 systems for compromise and apply patches immediately.
Independent investigators from Mandiant, CrowdStrike, NCC Group, and IOActive verified that F5’s build pipelines (the systems used to publish software updates) had not been altered. Still, the theft of sensitive source code means attackers could create powerful new exploits targeting F5 customers for years to come.
Who’s Behind It: The UNC5221 / BRICKSTORM Group
Multiple intelligence sources, including Google’s Mandiant, attribute the breach to a Chinese state-sponsored threat group known as UNC5221, operating under the broader espionage campaign BRICKSTORM.
This group specialises in targeting network appliances and edge devices — the routers, firewalls, and gateways that connect organisations to the internet — because these systems often lack the monitoring tools found on normal computers.
UNC5221’s fingerprints include:
Long-term, stealthy presence inside victim networks (average dwell time: 12+ months)
Custom-built malware written in Go, named BRICKSTORM, designed for Linux and Windows systems
Techniques drawn from the MITRE ATT&CK framework, including:
Credential theft
Exploitation of public-facing applications
Lateral movement through IT networks via SOCKS proxy tunnels
Data exfiltration disguised as normal network traffic to evade detection.
Who’s at Risk: Known UK and EU Customers of F5
Because F5’s customer list is largely public through case studies and procurement records, we can see just how deeply embedded its systems are in European infrastructure. These organisations use or have used F5 products such as BIG-IP, NGINX Plus, and Access Policy Manager (APM) — all potentially exposed by this breach.
UK Public Sector and Critical Services
Department for Work and Pensions (DWP) – Uses NGINX Plus to secure citizen-facing services and benefits systems.
Scottish Government – Relies on BIG-IP for load balancing, identity management, and web-application firewalls protecting agricultural subsidy platforms.
Scottish Wide Area Network (SWAN) – A £350 million connectivity network linking 6,000 public sites (schools, councils, hospitals) — many use F5 through BT contracts.
NHS Trusts –
Lancashire Teaching Hospitals NHS Foundation Trust: uses F5 APM for secure staff remote access.
NHS Lothian: uses BIG-IP DNS for high availability between data centres.
Spire Healthcare: secures its digital services with F5 technology.
UK Police & Local Councils – Several local authority IT frameworks list F5 as a core supplier for secure access gateways.
European Public Sector
European Commission IT Services (DIGIT) – Uses F5 for secure load balancing in internal systems.
German Federal Employment Agency (Bundesagentur für Arbeit) – Reported deployments of F5 for access management and WAF protection.
Dutch Tax and Customs Administration (Belastingdienst) – Known user of BIG-IP for application delivery and identity control.
French Ministry of the Interior – Longstanding F5 client for load balancing within secure networks.
Financial Services
HSBC UK – Deployed F5 for secure API management in open banking applications.
Deutsche Bank, Santander, and BNP Paribas – Listed among European financial institutions using F5 for application security and regulatory compliance.
Telecoms and Utilities
BT, Vodafone, Virgin Media, and Deutsche Telekom – Rely on F5 for DNS, load balancing, and DDoS protection.
National Grid and EDF Energy – Identified in vendor ecosystems as F5 users for secure operational technology networks.
Enterprise and Manufacturing
BP, Shell, Unilever, and AstraZeneca – Have all deployed F5 systems for hybrid cloud or internal application delivery.
Siemens, Airbus, and SAP – Integrate F5 appliances for global network security and access management.
In short, nearly every major enterprise or government across Europe that depends on digital traffic management or load balancing likely runs F5 technology somewhere in its Technology stack.
Why They Did It
The motivation behind the F5 breach appears strategic rather than financial.
Espionage and intelligence gathering – Access to F5’s source code provides visibility into how thousands of organisations defend their networks.
Zero-day discovery – By analysing F5’s code, attackers can find new, undisclosed vulnerabilities before they’re patched.
Supply chain leverage – Compromising one trusted vendor gives access to a global client base, from ministries to megabanks.
Preparation for future cyber conflict – Pre-positioning malware or exploiting knowledge of F5 systems could provide a tactical advantage in future geopolitical crises.
This isn’t about stealing money — it’s about control and insight.
What This Means for the UK and Europe
The consequences for the UK and EU could be serious:
Public services at risk – Government departments, hospitals, and councils using F5 may face follow-on attacks.
Data exposure – Citizen records, patient data, and financial information could be targeted.
Supply chain shock – The compromise undermines trust in the very companies meant to provide security.
Economic risk – If attackers develop new zero-day exploits using stolen F5 code, those vulnerabilities could ripple through critical industries.
The NCSC has warned that this is not a one-off incident but part of a “systemic campaign” targeting trusted technology providers.
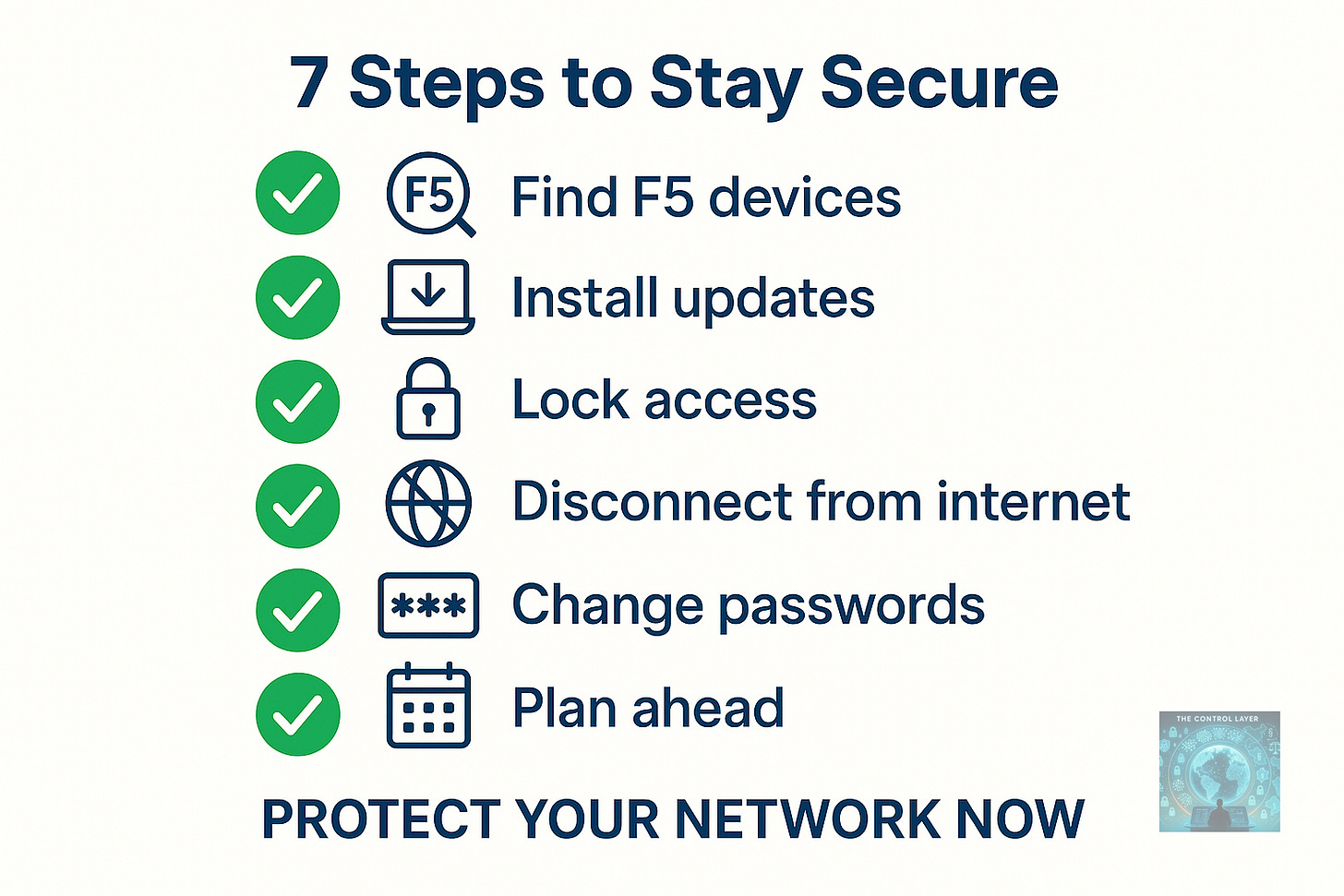
What F5 Customers Should Do Now (Plain English Guide)
You don’t need to be an engineer to take the right steps.
Here’s what every organisation using F5 products — from hospitals to small businesses — should do right now:
Find out where you use F5
Make a list of every system or service in your organisation that uses F5 equipment or software (BIG-IP, BIG-IQ, NGINX Plus, etc.).
Install the latest updates
Go to F5’s website or talk to your IT provider and make sure all your F5 devices are fully patched. This closes known security holes.
Lock down who can log in
Check that only authorised staff can access your F5 management console. Use multi-factor authentication (MFA) — a code on your phone as well as a password.
Disconnect from the public internet
F5 devices should not be reachable from outside your organisation. If they are, move them behind a firewall or restrict access to a secure internal network.
Change saved passwords and keys
If your F5 systems store login credentials or API keys, reset them. Stolen source code could help attackers guess how those keys work.
Look for unusual activity
Review system logs for anything odd — failed logins, unknown IP addresses, or unexpected data transfers. Report concerns to your IT team or to the NCSC.
Plan for the future
Assume this could happen again. Create a backup plan for your most important systems, and practice what you would do if one went offline.
These are not just IT tasks — they’re business survival actions.
What We Can Learn
The F5 breach underlines a simple truth: trust is not security.
Even the companies that protect the internet can themselves become the weak link.
To build resilience, organisations should:
Treat every vendor as a potential point of failure
Build layered defences so one breach doesn’t topple everything
Share threat intelligence quickly and openly
Invest in rapid detection and recovery, not just prevention
As the NCSC said in its advisory: “The attackers are already inside. The question is how fast we find them.”
The Bottom Line
The F5 breach is a wake-up call for every country that depends on digital infrastructure.
It shows that state-backed hackers are no longer probing the edges of the internet — they’re burrowing into its foundations.
From the NHS to national power grids, from cloud data centres to local councils, the message is clear: the next war won’t start with tanks. It will start with code.