701 Victims and Counting
Why Qilin's Healthcare Dominance Should Alarm Every UK Board
Why it matters: Qilin ransomware claimed 701 victims in 2025—a 290% increase that includes the first confirmed UK fatality linked to a cyber attack. The 18-month Synnovis investigation closure reveals what “worst case” actually looks like, and why boards can no longer treat ransomware as an IT problem.
In June 2024, Qilin ransomware operators encrypted systems at Synnovis, the pathology laboratory serving several London NHS trusts. They demanded $50 million. Synnovis refused to pay. The attackers published 400GB of patient data, including blood test results, NHS numbers, and hospital arrangement documents [1].
The attack postponed over 320 operations at King’s College and Guy’s and St Thomas’ hospitals in a single week. More than 1,294 outpatient appointments were cancelled. Blood supplies ran short across southeast London [2].
In June 2025—a full year later—King’s College Hospital NHS Trust confirmed what many had suspected: the ransomware attack was a significant contributory factor in at least one patient death [3].
In November 2025, Synnovis finally closed its forensic investigation. Eighteen months. That’s how long it takes to fully assess what a sophisticated ransomware group stole when they had unrestricted access to healthcare systems.
The estimated cost to the NHS exceeds £32 million [4]. The $50 million ransom demand, by comparison, looks almost reasonable.
Qilin’s 2025 dominance isn’t an accident
Synnovis wasn’t an isolated incident. Qilin ransomware group claimed 701 victims in 2025, with 118 attacks independently confirmed and 788,377 records verified as breached [5]. The group stole an estimated 116 terabytes of data across healthcare, government, manufacturing, and education sectors.
The 290% increase from April 2025 coincided with RansomHub’s disappearance. When that rival operation went dark, its affiliates migrated to Qilin—bringing their skills, access, and appetite for high-value targets [5].
Healthcare remains the preferred sector. Qilin conducted 45 healthcare attacks in 2025, with 14 independently confirmed [5]. The logic is grimly rational: healthcare organisations hold highly sensitive data, operate under intense time pressure, and often run legacy systems that can’t be easily patched.
The Covenant Health attack (December 2025) exposed 478,188 patients’ records. Attackers maintained access for eight days before detection. That’s typical dwell time for Qilin in healthcare environments.
The ransom payment calculus has shifted
The conventional wisdom on ransomware payment has evolved. UK and EU policy discourages payment, arguing it funds criminal enterprises and provides no guarantee of data recovery. Synnovis followed this guidance, refusing the $50 million demand.
The actual recovery cost—£32 million in direct expenses plus 18 months of operational disruption—suggests the economics are more complex than policy statements acknowledge [4].
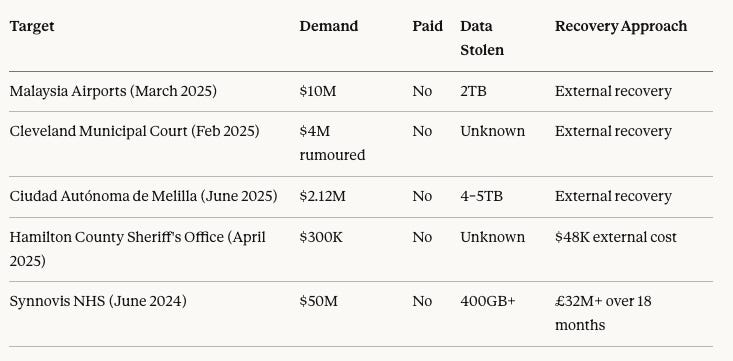
Consider the ransom demands across Qilin’s 2025 campaign:
Analysis: No confirmed high-profile payments in 2025 suggest either successful suppression of payment disclosures or genuine hardening of victim resistance. The Hamilton County case is instructive: a $300,000 demand resulted in $48,000 recovery costs—a ratio that favours non-payment. But Synnovis demonstrates that healthcare complexity can invert this calculus dramatically.
Why boards can’t delegate this anymore
The Synnovis incident illustrates three governance failures that boards must address directly.
First, detection timelines matter more than defence investments. Qilin attackers typically maintain access for eight or more days before detection in healthcare environments [6]. That’s eight days to map systems, identify valuable data, establish persistence, and prepare encryption payloads. All the perimeter security in the world becomes irrelevant once attackers are inside and undetected.
Boards should ask: “How long would an attacker have undetected access in our environment?” If the answer is “we don’t know,” that’s the first problem to solve.
Second, incident response planning requires realistic recovery timelines. Synnovis initially estimated weeks for recovery. The investigation took 18 months. Business continuity plans that assume rapid restoration from backups often fail to account for forensic requirements, supply chain dependencies, and regulatory notification obligations.
Boards should test incident response plans against realistic scenarios, not optimistic assumptions. A tabletop exercise that assumes two-week recovery when actual recovery takes 18 months provides false confidence.
Third, ransomware is a patient safety issue in healthcare, not just a data protection issue. The confirmed fatality at King’s College Hospital transforms ransomware from a compliance matter to a clinical governance matter. Healthcare boards have a duty of care that extends beyond information security frameworks.
The healthcare sector’s structural vulnerability
Healthcare organisations face constraints that make ransomware defence unusually difficult.
Legacy systems: Medical devices, diagnostic equipment, and clinical systems often run outdated software that cannot be easily patched without risking functionality. A 2019 MRI scanner may run Windows 7 because the manufacturer never certified newer operating systems.
Operational continuity pressure: Healthcare cannot simply “shut down for maintenance.” Systems must remain available 24/7, creating pressure to defer security updates that require downtime.
Data sensitivity: Healthcare data commands premium prices on criminal marketplaces. A complete medical record—containing NHS number, date of birth, diagnoses, treatments, and prescriptions—enables identity theft, insurance fraud, and targeted extortion.
Supply chain complexity: The Synnovis attack affected multiple NHS trusts because they shared a common pathology provider. This concentration of services creates efficiency but also concentration of risk.
Analysis: These constraints are structural, not addressable through better training or more security tools. Boards must acknowledge that healthcare cyber risk is fundamentally different from other sectors and requires proportionate investment.
Risks and constraints
Attribution confidence for Qilin is high but not absolute. The group operates a Ransomware-as-a-Service model, meaning different affiliates conduct attacks under the Qilin brand. Technical tradecraft varies across affiliates, complicating defence strategies.
The 701 claimed victims figure comes from Qilin’s own leak site. While 118 attacks are independently confirmed, some claims may be exaggerated or duplicated. The 788,377 records and 116TB data figures are derived from confirmed incidents only.
Recovery cost estimates for Synnovis and other victims are approximations based on disclosed information. Actual costs—including reputational damage, patient harm, and long-term operational disruption—likely exceed reported figures.
What to do next
For boards and executives: Elevate ransomware from an IT risk to a strategic risk. Ensure the board receives regular briefings on detection capability, not just defence posture. Commission realistic incident response testing that accounts for forensic, legal, and regulatory requirements—not just technical recovery.
For technical leaders: Prioritise detection over prevention. Assume attackers will gain access; focus on reducing dwell time from days to hours. Implement monitoring for unusual data exfiltration patterns (large volumes leaving clinical systems should trigger alerts). Segment networks to contain lateral movement.
For mid-market organisations: If you’re not a healthcare provider but serve healthcare organisations, your security posture affects theirs.
The Cl0p Oracle EBS campaign covered in the following article demonstrated how attackers use business software vulnerabilities to breach healthcare systems. Ensure your systems don’t become the entry point for attacks on your customers.
Disclaimer: This article represents analysis based on publicly available information as of January 2026. It does not constitute legal, financial, or professional advice. Attribution to threat actors reflects reported information and may be subject to revision as investigations continue.
If your organisation needs support developing ransomware resilience that goes beyond technical controls, Arkava helps mid-market enterprises build governance frameworks that boards can actually use.
Contact: engage@arkava.ai