Britain’s Hidden Cyber Gap
Why the NCSC Says Our Machines Are the Next Frontline
New UK guidance exposes how hackers are now targeting the systems that move water, power, and transport — and why every operator must map their “Operational Technology” before it’s too late.
Why it matters
Critical services increasingly run on computers that move the physical world — pumps, conveyor belts, traffic lights, hospital HVAC. Criminals and state actors are now targeting those systems. The UK’s National Cyber Security Centre (with seven international partners) has published new guidance that raises the bar: you’re expected to keep a live, accurate map of your OT so you can;
Defend it,
Prove compliance,
Recover fast when things go wrong.
First, what is “Operational Technology” (OT)?
Think of OT as the computers that control physical processes. Where traditional IT handles emails and spreadsheets, OT runs machines.
Typical OT gear: programmable logic controllers (PLCs), remote terminal units (RTUs), sensors, actuators, engineering workstations, historian servers, Human–Machine Interfaces (HMIs).
Where you’ll find it: factories and food plants, utilities and water treatment, rail signalling and stations, airports and ports, road tunnels and flood defences and every Hospital and large building on Earth.
Everyday effect: OT keeps taps running, wards ventilated, trains moving and supermarkets stocked.
Example OT software (to make this concrete)
SCADA & HMI platforms: AVEVA (Wonderware) System Platform, GE iFIX/CIMPLICITY, Inductive Automation Ignition — used to visualise and control plants.
Engineering/PLC suites: Siemens TIA Portal, Rockwell Studio 5000, Schneider EcoStruxure Control Expert — used to program the controllers that run lines and pumps.
DCS (distributed control systems): Emerson DeltaV, Honeywell Experion — used in complex process plants.
Building & estate systems: Johnson Controls Metasys, Honeywell EBI — control HVAC, access, alarms.
You don’t need these exact brands to be “doing OT”; they’re simply relatable examples of the kinds of systems the guidance is about.
What changed — in one sentence
Eight national cyber agencies now expect organisations to create and maintain a “definitive record” of their OT architecture—a continuously updated, trustworthy view of assets, connections, data flows and suppliers—then use it to drive risk decisions, segmentation, vendor access and incident response.
The guidance in plain English (the five big ideas)
Keep a live map of your OT
List everything: devices, software versions, how they’re connected, who can reach them, and what they’re for. Pull from drawings, configurations, staff knowledge and safe monitoring. Avoid heavy active scans on fragile legacy kit unless you’ve tested them offline. Treat the map itself as sensitive.
Treat OT information like crown jewels
Put OT documents and configs into your information security management system (ISO/IEC 27001): classify, control access, back them up, audit changes. The attackers want your diagrams as much as your data.
Prioritise by consequence and exposure
Score each asset by criticality (safety/business impact), exposure (how reachable it is) and availability constraints (can it be patched or only during shutdowns?). Use those scores to decide where to segment first, where to harden, and where to add compensating controls. (This aligns with IEC 62443.)
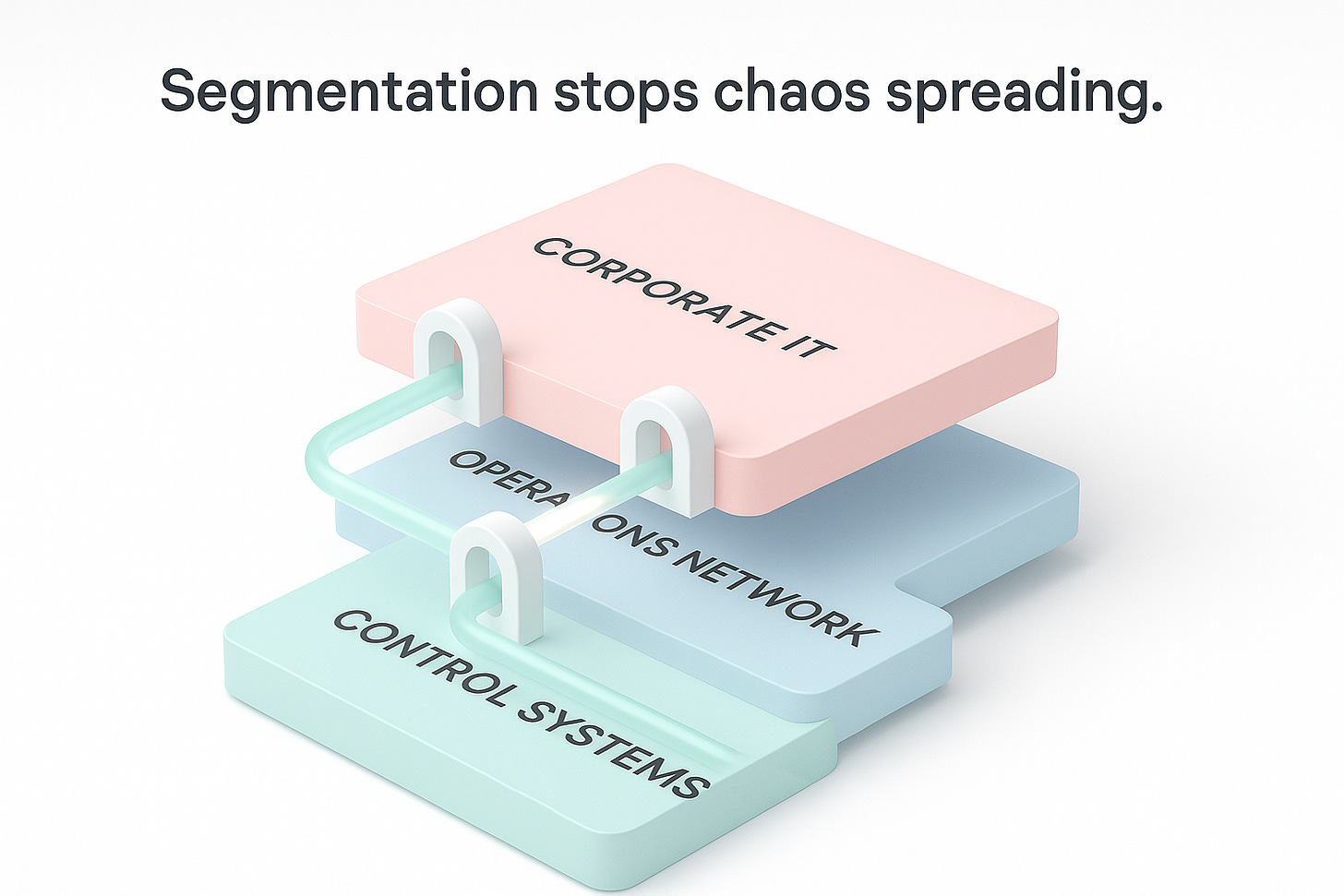
Document all connectivity
Most sites aren’t air-gapped. Draw the actual data flows — inside the plant and out to suppliers — and design network zones and conduits so problems can’t spread. This is the practical route to micro-segmentation.
Get serious about third-party access
Write down every supplier’s connection, trust level and support route. Move to just-in-time, recorded remote access with approvals — and kill always-on vendor tunnels.
Why the pressure is rising
Threats are sharper. OT-focused hacker groups (including those overlapping with Volt Typhoon —the Chinese state-sponsored Advanced Persistent Threat (APT) group) actively hunt for network diagrams and operating instructions; ransomware crews increasingly target manufacturers, utilities and healthcare to cause maximum pain fast.
Regulators are tightening.
UK: Cyber Security & Resilience Bill (CSRB) will harden incident reporting and oversight, and strengthen the role of the NCSC Cyber Assessment Framework (CAF). Expect your “definitive record” to become evidence in audits.
NCSC CAF v4.0 (Aug 2025) is more threat-led and outcome-based — you can’t evidence capability without up-to-date visibility.
EU: NIS2 enforces risk management across IT and OT, stricter supplier duties, 24-hour reporting, and director accountability. If you operate or supply into the EU, you’re likely in scope.
Who needs to act (and why)
Energy & utilities,
Water,
Transport,
Manufacturing,
Defence,
Food & drink,
Pharma,
Healthcare,
Local/national government,
Data centre,
All their suppliers/integrators.
If your equipment moves, heats, cools, mixes, signals or protects anything in the real world — or you support those who do — this applies to you. Insurers, auditors and procurement teams will end up asking for proof.
Leave a comment to be sent a Pragmatic 90-day action plan
My Practical tips (no jargon)
Collect before you scan. Old controllers can fall over if you probe them too hard. Start with documents, configs and passive monitoring. Test any active methods offline.
Treat drawings like code. Version them. Approve changes. Be able to roll back.
Segment by consequence, not convenience. Group things by what could go wrong together, not by historic VLANs.
Kill permanent vendor tunnels. Use time-boxed access with approvals and full session recording.
Back up configs (and rehearse restores). Most downtime is rebuild time.
Protect the record itself. Least-privilege access, encryption, tamper-evident logging, tested recovery.
What “good” looks like by year-end
A board-approved policy mandating a definitive OT record tied to change control.
Zones & conduits enforced on your riskiest systems; protocol allow-lists in place.
Supplier access is brokered, time-bound and recorded; standing admin accounts removed.
CAF v4.0 self-assessment linked to living diagrams and device lists, not an old SharePoint folder.
Contracts require suppliers to deliver updated as-built diagrams and SBOM/HBOM at handover.
The bottom line
You cannot defend what you can’t see. The “definitive record” is the new foundation for OT security, compliance and resilience. Start small, start now, and make the record living: if it’s not in the record, it didn’t happen.