Asahi’s ransomware hangover
what a beer shortage tells us about cyber-physical risk?
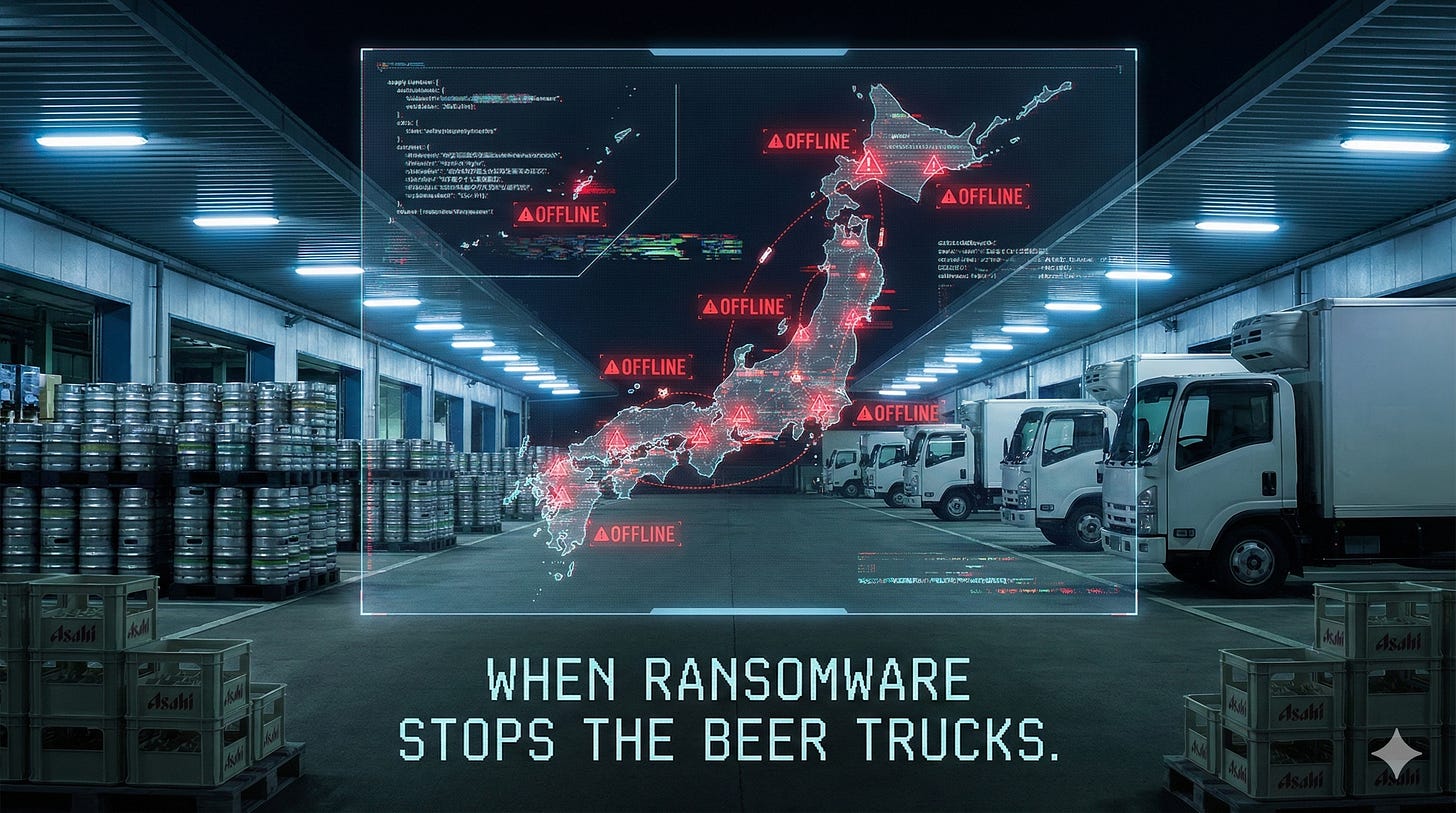
On 29 September 2025, Japan’s biggest brewer Asahi detected “system disruption due to a cyberattack” on its data centre. Within hours, order processing, shipping and call centres across Japan were shut down, production at 30 factories stalled, and staff were back to phones, fax and handwritten orders to keep beer moving.
Days later, the Russian‑linked Qilin ransomware group claimed responsibility on its dark web leak site, boasting of 27 GB of stolen data. By the end of November, Asahi confirmed the personal data of around 1.9 million people may have been exposed, and its full‑year financial results will be delayed more than 50 days beyond year‑end because core systems simply aren’t ready.
This is not “just” a data breach. It’s a live case study in what happens when ransomware hits an operational, physical supply chain.
Why it matters
If attackers can stop beer getting to shops, they can stop food, fuel or medicines too.
Asahi shows how one breach can simultaneously hit OT, IT, privacy, revenue and financial reporting.
UK and EU boards should treat this as a rehearsal for NIS2‑era resilience, not distant global news.
What actually happened to Asahi?
From data centre alert to nationwide disruption
Asahi’s timeline looks brutally familiar:
29 September 2025 – Asahi detects a cyber incident at its data centre and confirms a ransomware attack. As part of containment, it suspends domestic order placement, shipping and external email, and sets up an emergency response HQ.
Attackers are reported to have entered via equipment at a company site (a subsidiary facility), then moved laterally into the core network before deploying ransomware across multiple servers and employee PCs.
30 factories across Japan are affected. Six key breweries restart production by 2 October, but ordering and logistics systems remain heavily degraded.
With digital workflows down, staff revert to phone calls, paper order forms and manual scheduling. Asahi’s own updates talk about “partial manual order processing and shipment”; external reporting describes restaurants and retailers struggling with shortages and out‑of‑stock products.
In UK/EU terms, this is the nightmare convergence of IT compromise, OT disruption and supply chain failure that NIS2 and national cyber strategies have been warning about for years.
The breach at human scale: 1.9 million people
By late November, after almost two months of forensics, Asahi disclosed that up to 1.9 million individuals may have had personal data exposed.
Press reports and summaries of Asahi’s own statement break the numbers down roughly as:
1,525,000 customers who contacted Asahi’s service centres for beers, soft drinks or foods
107,000 employees and former employees
168,000 family members of employees, including families of retirees
114,000 external contacts, including people who received ceremonial telegrams from Asahi
The exposed fields vary by group, but typically include names, gender, postal addresses, phone numbers and email addresses. For employees and their families, data may also include date of birth and other HR details.
Asahi stresses that:
There is no evidence of credit card data being compromised.
So far, only a small number of employee records stored on specific laptops have been confirmed as actually accessed, though the potential scope is much wider.
Under UK GDPR and EU GDPR, an organisation in the same position would almost certainly be dealing with a notifiable personal data breach, requiring notification to the relevant authority within 72 hours of becoming aware of it, and communication to affected individuals where there is a high risk to their rights and freedoms.
The human risk is not abstract. This kind of dataset is perfect fuel for:
Convincing phishing and telephone scams
Identity theft and new‑account fraud
Targeted social engineering of employees, partners and VIP customers
Block the ransomware, and you still have the privacy problem.
Who are Qilin – and why do they matter here?
Qilin (also known as Agenda) is a ransomware‑as‑a‑service (RaaS) group first observed in 2022 and widely assessed as Russian‑linked. They run a classic double‑extortion model: encrypt data and systems, and steal data for separate blackmail and leak threats.
By late 2025, open‑source tracking suggests Qilin has become one of the most prolific ransomware operators globally, with hundreds of claimed victims and at least 70 attacks in a single 30‑day period. High‑profile cases include the Synnovis incident impacting the NHS pathology supply chain in the UK, and attacks on manufacturers, local authorities and critical services.
Their playbook overlaps strongly with what we know about the Asahi case:
Initial access via stolen or phished credentials and exposed remote services
Lateral movement across the network, sometimes using common admin tools
Destruction or encryption of backups and logs
Data exfiltration before encryption (so paying the ransom doesn’t guarantee privacy)
Asahi isn’t just unlucky. It’s part of a much wider industrial and supply chain targeting trend, which UK NCSC and ENISA have both flagged as a priority threat.
“When a brewery goes manual because of ransomware, that’s not a quirky tech story. It’s proof that cybercriminals can reach deep into physical life.”
Operational and financial impact: from beer taps to the balance sheet
The Asahi incident is unusually transparent about business consequences – which makes it useful for boards outside Japan.
Key impacts reported so far:
30 domestic factories affected, with production halted or severely disrupted; six key plants restarted production by 2 October.
Prolonged disruption to order processing, shipping, call centres and customer service, forcing the use of “pen and paper” and manual workarounds.
Product shortages at restaurants and retailers across Japan, including a visible “beer shortage” narrative in domestic media.
Sales decline: October sales at key Japanese beverage and food units reportedly fell by roughly up to 40% year‑on‑year because orders couldn’t be fulfilled.
Financial reporting delay: Asahi’s own investor notice confirms that full‑year results for the fiscal year ending 31 December 2025 will be delayed beyond the usual 50‑day window while systems and closing processes recover.
Recovery horizon: Logistics are expected to “normalise” only around February 2026, and even then not all products will be shippable.
This is textbook business continuity and governance exposure. Under UK/EU regimes like NIS2 and national corporate governance codes, boards are expected to understand and manage exactly this kind of operational risk, not treat it as an IT side issue.
To pay or not to pay: Asahi’s stance and UK/EU expectations
Asahi’s CEO Atsushi Katsuki publicly apologised and took a clear stand: reports quote him saying that even if there had been a ransom demand, the company “would not have paid it”.
That position aligns strongly with where UK and EU policy are heading:
The UK government and NCSC explicitly do not condone paying ransoms, and new guidance stresses that paying does not meet regulatory obligations and may raise sanctions risks.
Proposals published in 2025 would ban public sector bodies and operators of critical national infrastructure from paying ransoms altogether, with mandatory reporting for others.
EU law does not currently ban ransom payments, but ENISA and law‑enforcement‑aligned guidance emphasise that payments fuel the criminal business model and offer no guarantee of decryption or non‑disclosure.
For boards, this means:
You should assume you will not pay – either because it is illegal, prohibited by policy, or tactically unwise.
Your resilience and recovery planning must be good enough that “we’re legally barred from paying” does not translate into “we go out of business”.
Asahi’s case shows both sides of that coin. On one hand, it refused to engage with Qilin and is investing in restoration and strengthened security instead. On the other, it is still facing months of disruption, delayed results, and reputational damage.
Lessons for UK and EU organisations
This section is analysis and opinion based on publicly reported facts and current UK/EU guidance.